Profiling OT Network Traffic
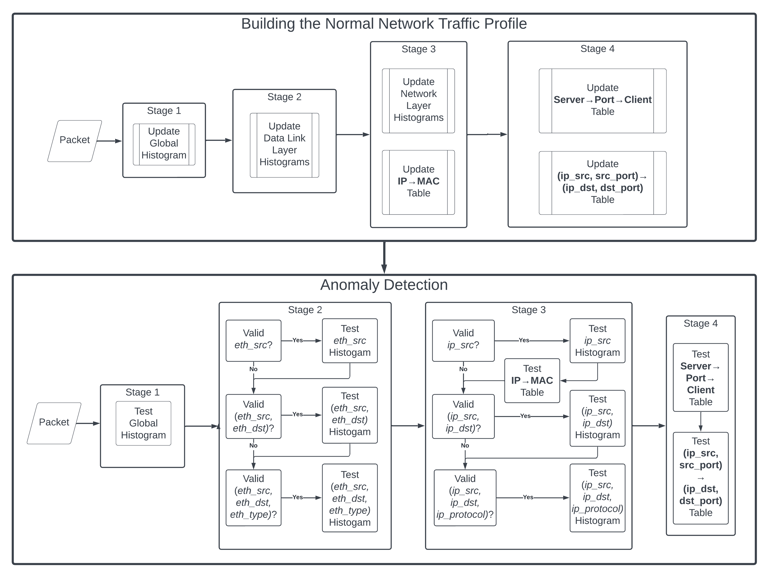
The top part of the flowchart, "Building the Normal Network Traffic Profile," serves as the foundation for all three of my published works.
The Normal Profile is crucial for detecting anomalies (see my first paper). The method for doing so is enhanced in the second paper, and my third paper uses the Normal Profile to fingerprint devices, rather than for anomaly detection.
Enhancing Anomaly Detection
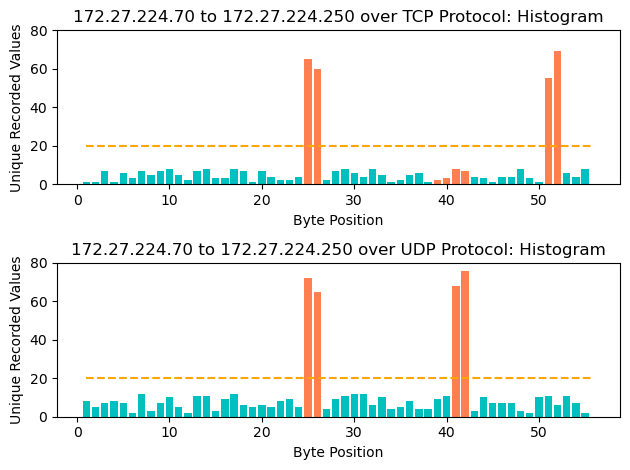
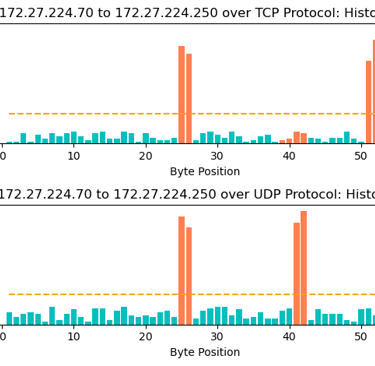
In my second paper, "Enhancing Intrusion Detection in Industrial Control Systems: An Adaptive Protocol-Agnostic Approach," the "field mask" and "thresholding" methods are added to the anomaly detection process.
These features enabled our model to detect anomalies in unlabed datasets - which the original model struggled to do.
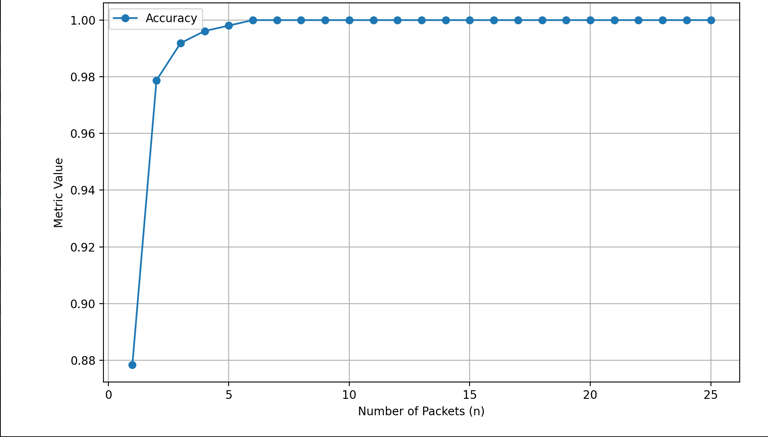
Device Fingerprinting
The third paper built off the Normal Profile uses it to identify packets rather than detect anomalies. The graph illustrates the device identification accuracy for various values of k used in the Jensen-Shannon Divergence (JSD).

